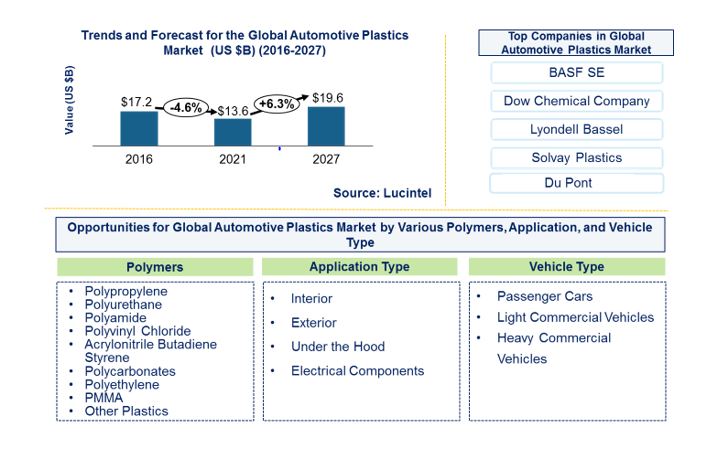
Trends and Forecast for the Global Automotive Plastics Market Trends, opportunities and forecast in automotive plastics market to 2027 by polymer (polypropylene, polyurethane, polyamide, PVC, ABS, polycarbonates, polyethylene, PMMA and other plastics), by vehicle type (passenger cars, light commercial vehicles, and heavy commercial vehicles), by application (interior, exterior, under the hood and electrical components), and […]









